Concord Technologies Completes Acquisition of Biscom, Inc. to Create a New Industry Leader in the Secure Transmission and Intelligent Handling of Protected Information Seattle, WA – January 5, 2024 – Concord Technologies (“Concord”), a leading provider of...
Biscom's Press Releasess
News and announcements from Biscom
Press Release: Biscom Appoints David Lucey As New CEO
WESTFORD, MA - May 31, 2022 -- Biscom, Inc., a leading provider of secure fax and document delivery, announced today that David Lucey has been appointed new CEO of the company. Lucey comes to Biscom with over 30 years of experience in developing healthcare technology...

Press Release: ParkerGale Invests in Secure Document Delivery Solutions Company, Biscom
WESTFORD, MA, January 13, 2022: Biscom, Inc., a leading provider of enterprise fax and secure file transfer solutions for large enterprises in highly regulated industries announced today it has received a majority investment from ParkerGale Capital (ParkerGale). Terms...

Biscom announces Cerner Millennium validation of Biscom Enterprise Fax
Biscom Enterprise Fax for Cerner Millennium leverages industry standard FHIR APIs to enable faxing directly from patient records. Biscom Enterprise fax for Cerner Millennium streamlines electronic faxing by offering the following advanced features: A user can initiate...
PRESS RELEASE: Biscom Cloud Fax Advanced
Contact Information:[email protected] BISCOM LAUNCHES 2ND GENERATION CLOUD FAX PLATFORM Biscom Cloud Fax Advanced has launched with support for Biscom's latest web client and end-to-end security WESTFORD, MA -- AUGUST 25, 2021 -- Biscom, a leading provider of...
Biscom Closes 2019 With Another Record Year of Revenue Growth
A Leading Provider of Secure Document Transfer Biscom For the second consecutive year, Biscom sees double-digit revenue growth, as it delivers new cyber solutions in document delivery for highly regulated industries WESTFORD, MA -- January 14, 2020 -- Biscom, a...
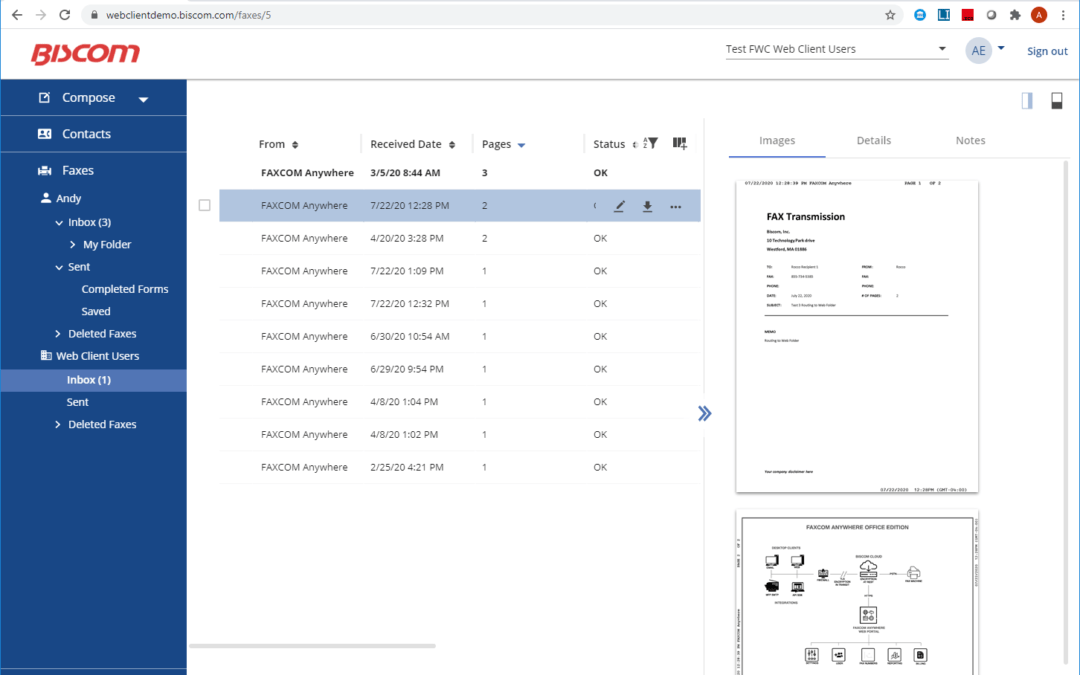
Biscom Introduces Next Generation of FAXCOM Web Client
Based on user feedback, new look continues Biscom’s mission to advance secure document delivery solutions for industries that rely on them most WESTFORD, MA – December 17, 2019 – Today, Biscom, a leading provider of...
Biscom powers HP Healthcare Edition Portfolio to Provide Fax and Secure Messaging from HP MFPs
Improve Patient Security End-to-end print and PC portfolio improves patient safety, care coordination, clinical efficiency and security News highlights: Sanitizable keyboards and touch-enabled control panels through nitrile, latex and surgical gloves help prevent the...
Biscom Named as Finalist in 2019 Software as a Service Awards
International Software Awards Program Recognizes Biscom Transit, Biscom’s Cloud-based Secure Messaging Solution WESTFORD, MA – July 30, 2019 – Biscom, a leading provider of secure document delivery for regulated industries, today announced that Biscom has been...
Biscom Named 2019 MedTech Breakthrough Award Winner for Best Electronic Health Record Security Solution
MedTech Breakthrough Awards recognizes Biscom Transit, a cloud-based secure messaging solution from Biscom WESTFORD, MA - June 5, 2019 - Biscom, a leading provider of secure document delivery for regulated industries, today announced that Biscom Transit has been...
